Project Overview
In the modern era of technology, high-performance computing has become a necessity. However, enterprise licensing costs often become a barrier. This project explores OpenStack as a cost-effective solution for heavy workloads such as AI. It proves that building high-performance infrastructure does not have to be expensive
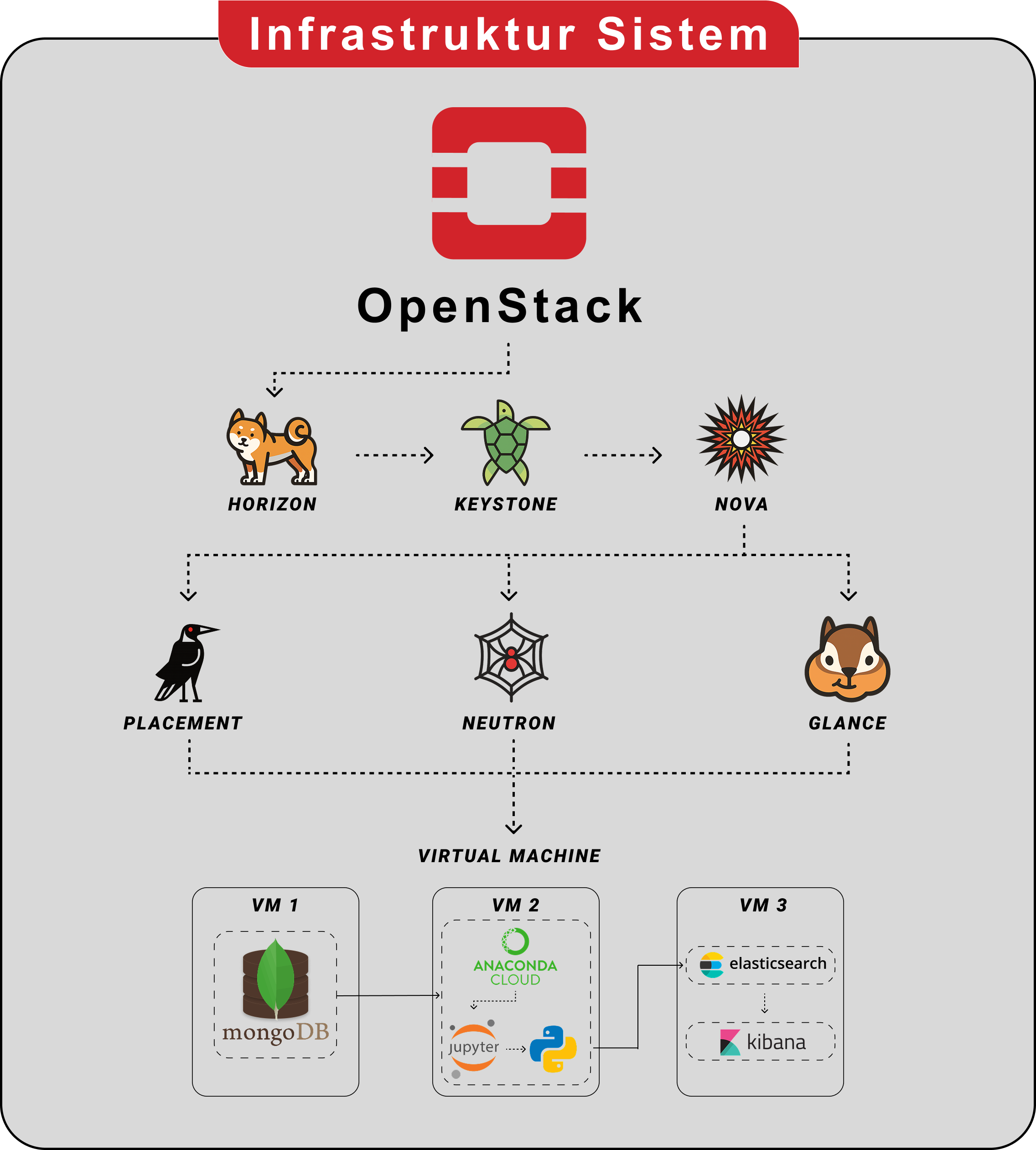
System Architecture
Horizon (Dashboard)
The web-based dashboard used to manage and monitor the entire cloud infrastructure.
Keystone (Identity)
The identity service that handles authentication and authorization for all users and services.
Nova (Compute)
The compute engine responsible for managing and provisioning virtual machines (instances).
Neutron (Networking)
The networking component that manages virtual networks, IP addresses, and connectivity.
Glance (Image)
The image service used to store and manage the virtual disk images needed to boot instances.
Key Features
Database VM (MongoDB)
Stores and manages large datasets required for AI analysis efficiently.
AI Engine VM
Equipped with Anaconda, Jupyter, and Python for model training and analysis.
Monitoring VM
Dedicated to system health tracking to ensure stable infrastructure.
Full Scalability
Placement service optimizes resource allocation across CPU, RAM, and Disk.
System Flow
Data Collection
Honeypot T-Pot captures attack interactions and records logs and payloads in the primary database.
Pre-processing
VM 2 extracts files and normalizes log data into a consistent format suitable for analysis.
Dual Analysis
The system performs static signature checks and dynamic runtime monitoring to identify malicious behaviors.
AI Classification
Processed data is fed into an AI model to generate threat scores and risk categories.
Indexing and Visualization
Results are indexed in Elasticsearch and displayed on Kibana for real-time monitoring and research.
Project Outcome
The project successfully established a functional OpenStack private cloud capable of handling diverse workloads. It achieved an end-to-end automated pipeline for malware analysis, from honeypot capture to AI-based classification and visualization. The implementation demonstrates that organizations can maintain full operational control and data sovereignty while running scalable, high-performance security infrastructures.
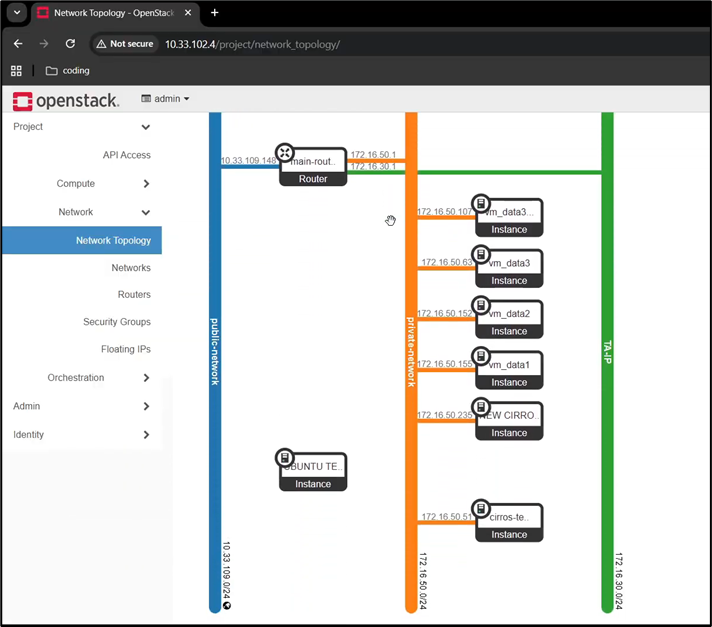
Screenshots